You can find a detailed description of the tunnel parameters in an article.
Note:
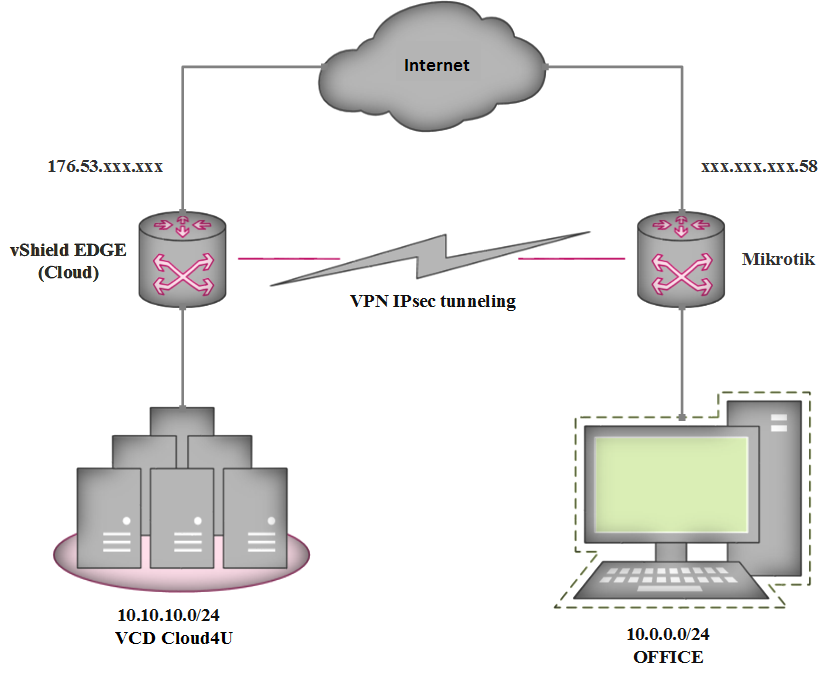
176.53.182.35 – external IP-address of your Edge Gateway
10.10.10.0/24 – local network connected to your Edge Gateway
176.53.182.58 – external IP-address of your router Mikrotik
10.0.0.0/24 – local network connected to your Mikrotik
The connection setup is carried out in two stages.
Stage 1: Mikrotik hardware setup.
Stage 2: configure the Edge Gateway on a remote server.
Stage 1:
In the drop-down menu on the 'IP' tab, select 'IPsec'.
Select the 'Peers' tab and click 'Add new' to create a new connection.

In the window that opens, enter the following values:
Name: Connection name
Address: the external IP address of your Edge Gateway.
Local Address: the external IP address of your Mikrotik router.
Select 'Exchange Mode' and choose 'IKE2'.

Click on the tab marked 'Proposals' and select 'Add new'.

Specify the name in the "Name" field.
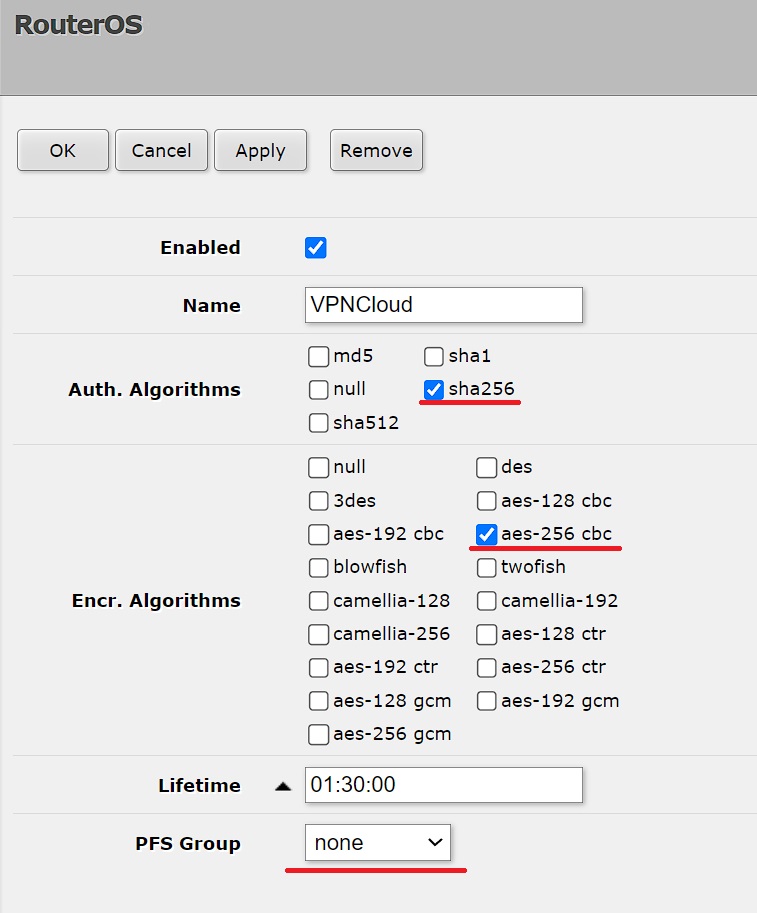
Auth. Algorithms - select SHA-256.
Encr. Algorithms – tick aes-256 cbc
PFS Group – select modp2048
Go to the 'Identities' tab and click 'Add new'.
In the 'Peer' field, select the connection that was created earlier.
In the field 'Auth. Method', select 'pre-shared key'.
Enter a password for the connection in the field labelled 'Secret'. Please write down the password. You will need it during Stage 2.
In the 'Notrack Chain' field, select the 'Prerouting' option.

Go to the 'Policies' section. Click 'Add new'.

In the 'Peer' field, select the connection that was created earlier.
Tick the 'Tunnel' parameter.
«Src. Address': enter the local network address connected to your Mikrotik.
'Dst. Address': the local network address connected to your Edge Gateway.
In the field 'Action', select 'Encrypt'.
In the 'Level' field, select 'Require'.
In the 'IPsec Protocols' field, select ESP.
In the 'Proposal' field, select the profile created earlier.

Go to the 'Profiles' tab and click on 'Default'.

Change the settings to the following values:
Hash algorithm: sha256
Encryption algorithm: aes-256.
DH group: modp2048.

Go to the 'Firewall' submenu, then click 'Add New' on the 'Filter Rules' tab.

In the 'Chain' field, select 'Forward'.
In the field 'Src. Address', enter the local network address connected to your Edge Gateway.
In the field 'Dst. Address', enter the local network address connected to your Mikrotik.
On the 'Action' tab, select 'Accept'.


Repeat these steps to add the rule to the firewall, but this time enter the local network address connected to your Mikrotik in the 'Src.' field. Address' field, enter the local network address connected to your Mikrotik. In the 'Dst. Address', enter the local network address connected to your Edge Gateway.

Go to the 'NAT' tab and click 'Add New' to select a new rule.

In the 'Chain' field, select 'Forward'.
In the field 'Src. Address', enter the local network address connected to your Mikrotik.
In the field 'Dst. Address', enter the local network address connected to your Edge Gateway.

Select a different rule. Change the values of 'Src. Address' and 'Dst. Address'.
The result should be two 'mirror' rules.

Go to the 'RAW' tab and click 'Add New'.

In the 'Chain' field, select 'prerouting'.
In the field 'Src. Address', enter the local network address connected to your Mikrotik.
In the field 'Dst. Address', enter the local network address connected to your Edge Gateway.

Create one more rule where, in the 'Src.' field, Address', enter the local network address connected to your Edge Gateway. In the 'Dst. Address', enter the local network address connected to your Mikrotik.
The result should be two 'mirror' rules.

Stage 2:
Go to your personal account and select your preferred data centre.
.
In the 'Networking' menu, select the 'Edges' submenu.

Select your connection and click 'CONFIGURE SERVICES'.

In the window that opens, select the 'VPN' tab.
Select the sub-tab 'IPsec VPN' and go to the sub-menu 'IPsec VPN Sites'.
Click '+' to set up the connection.

In the window that appears, move the 'Enabled' slider to the active state. 'Enable perfect forward secrecy (PFS)' must be disabled because problems are observed when this option is enabled and the tunnel may fail. We therefore recommend disabling PFS. In the 'Name' field, enter the name of your connection.
In the fields 'Local ID' and 'Local Endpoint', enter the external IP address of your Edge Gateway.
In the 'Local Subnets' field, enter the local network address connected to your Edge Gateway.
In the fields labelled 'Peer ID' and 'Peer Endpoint', enter the external IP address of your Mikrotik router.
In the field 'Peer Subnets', enter the local network address connected to your Mikrotik router.

Select the following settings:
Encryption algorithm: AES256.
Authentication: PSK.
In the 'Pre-Shared Key' field, enter the password that you wrote down. You entered it in the Mikrotik settings in the 'Secret' field.
Select the following settings:
Diffie-Hellman group: DH14.
Digest algorithm: SHA-256.
IKE option: IKEv2.
Session type: policy-based session.
Click 'Keep' to save the changes.

Go to the 'Activation Status' tab and activate the 'IPsec VPN Service Status'.

